
NOTE: THIS POST HAS SOME GLARING ERRORS. I am keeping it for posterity, but please note that the correct post is available here
I’m going to start this post off with a disclaimer - I’m still not fully happy with this solution. I would like to rely on RBAC controls within ConfigMgr to handle access to the AdminService through Cloud Management Gateway, but I have yet to discover a method to do so. When I do come up with a better method, I will update this post. However, at this point this appears to be the best way to secure access to the AdminService through CMG. Additionally this post is a setup to some future posts regarding integrating the Microsoft Power Platform with ConfigMgr, so do the work now to enjoy my future posts.
Second things second - I would like to thank Yinghua (Sandy) Zeng and Adam Gross for the road they have paved in this area. Adam’s resources on the AdminService available here and Sandy’s resource on accessing the AdminService via the CMG available here have been instrumental to this post.
Sandy’s post lays a good groundwork on how to access the AdminService via CMG, but the method used opens up the access to the AdminService to ALL users who belong to the tenant (or any tenant, if you setup the App Registration with multi-tenancy). This is obviously not optimal, especially since the AdminService has now exposed WMI methods in addition to just the read-only endpoints which were available originally.
The Basics
The basics to getting access to the AdminService via CMG are as follows:
- A properly configured Cloud Management Gateway (preferably with a cert from a public CA like Let’s Encrypt)
- SMS Provider Role configured to allow AdminService traffic through the CMG
- An app registration configured for web redirection (covered in this post)
- Account(s) synchronized to Azure AD (to get the necessary token)
Configuring the SMS Provider Role
This post assumes that you have a Cloud Management Gateway already configured. If you do not, Microsoft has a great guide available here. When you’ve gone through the process of creating a Cloud Management Gateway you’ll remember that you’ve had to allow access to various services (MP/SUP) via the Cloud Management Gateway. To enable AdminService access, we need to find a SMS Provider (likely on your primary site) and check a box. The ConfigMgr development team makes these things almost too easy :)
Launch your ConfigMgr console, go to the “Administration” blade, expand “Site Configuration”, click on “Servers and Site System Roles”, click on a site system with the SMS Provider role, right-click on the SMS Provider role and then select Properties.
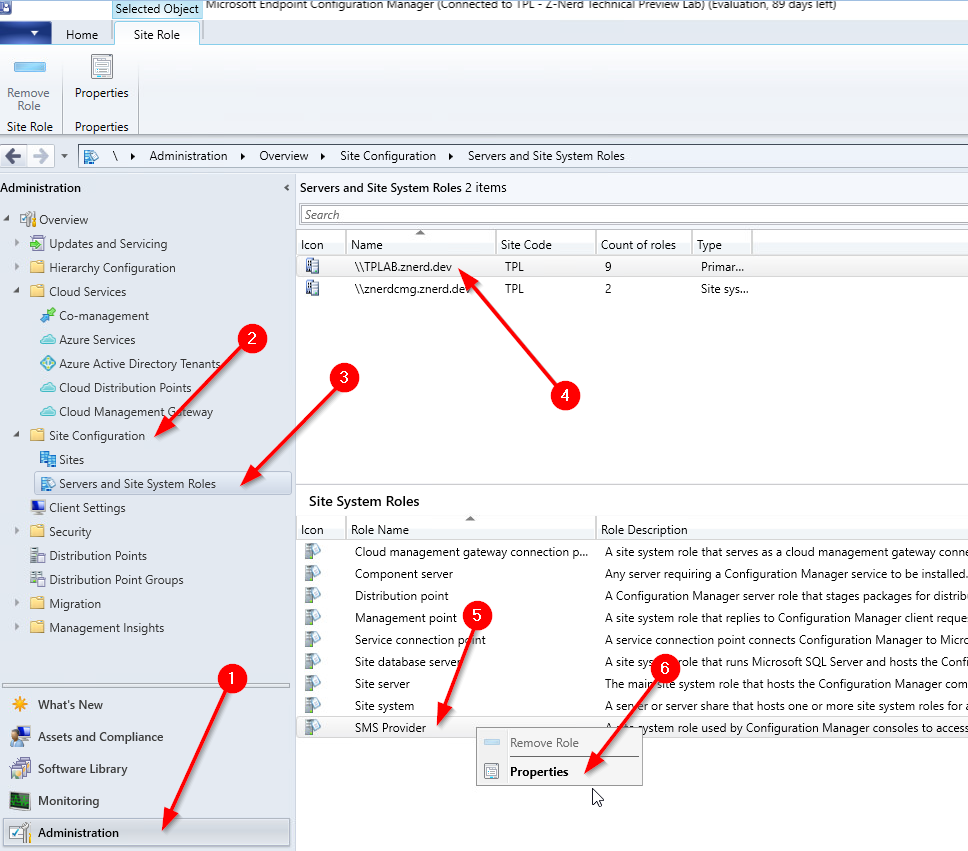
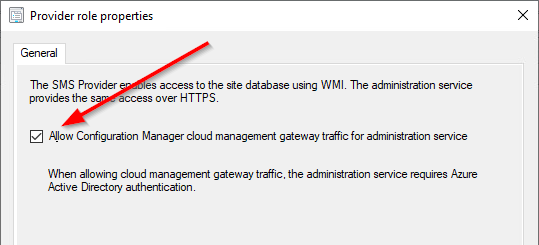
Once inside we just need to check the box to “Allow Configuration Manager cloud management gateway traffic for administration service”
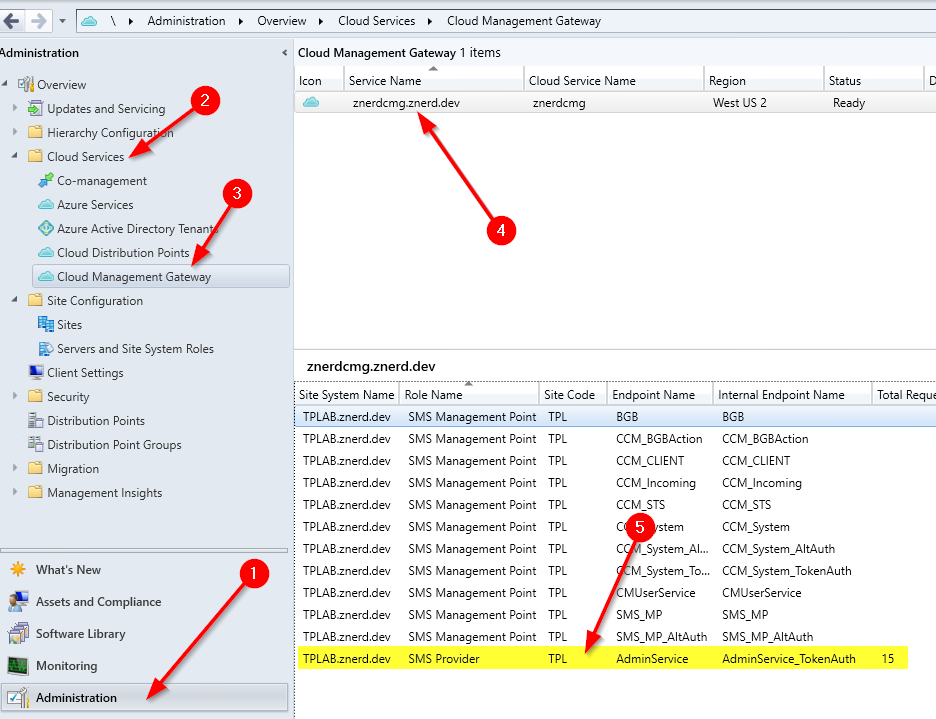
We can validate that the endpoint is available by looking at the Cloud Management Gateway’s “Role Endpoints” tab. On the “Administration” blade expand “Cloud Services”, select “Cloud Management Gateway”, select your Cloud Management Gateway, and then select the “Role Endpoints” tab. You should see a role with the name “SMS Provider” with an endpoint name of “AdminService”
Once we have the endpoint configured, we need to create a way to access it… securely.
Creating the App Registration
When you created your Cloud Management Gateway, two App Registrations were created in your Azure AD tenant. One which is a “Native” app registration for client connectivity and one which is a “Web” app registration which registers the web API with AAD. To manage access to the AdminService we need to create a third app registration.
Logon to your Azure Portal and search for and select “App Registrations”.
On the App Registrations page create a new registration. You can name it whatever you like provided that it is unique in your tenant. Additionally, I would recommend leaving the “Accounts in this organizational directory only” / “Single tenant” radio button selected unless you have a need to give access to users in a different tenant. You don’t need to configure a Redirect URI at this point.
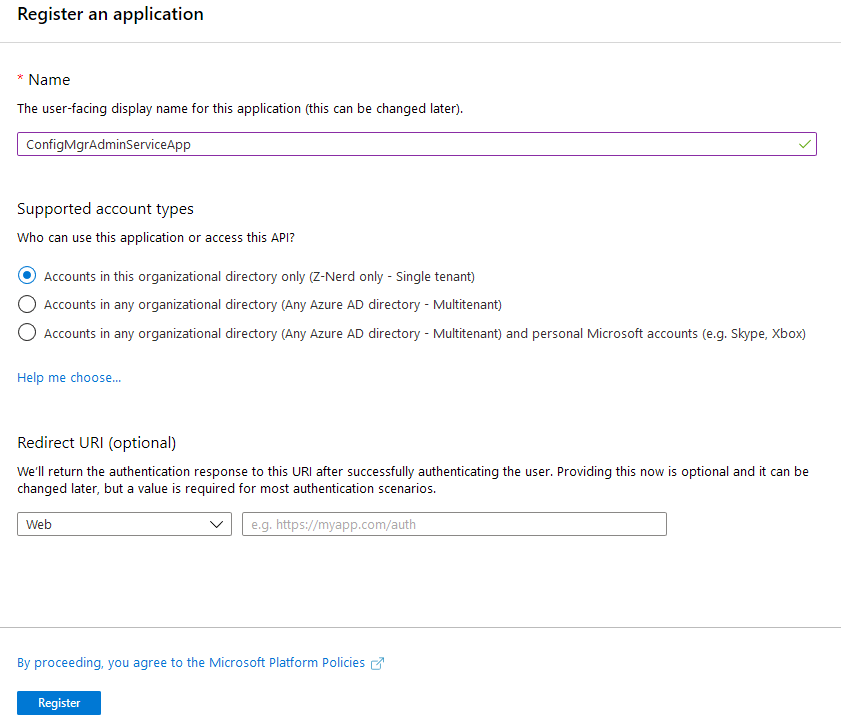
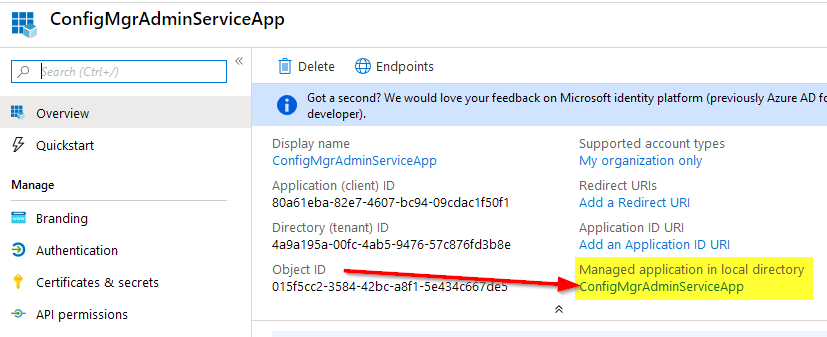
Once you’ve created your app registration, you need to limit access to it. On the “Overview” tab, locate the link below “Managed application in local directory” and then click on it. This will redirect you to the “Enterprise Apps” blade for this App Registration.
Click on the “Properties” tab, press the “Yes” button for User Assignment, and then press the Save button.
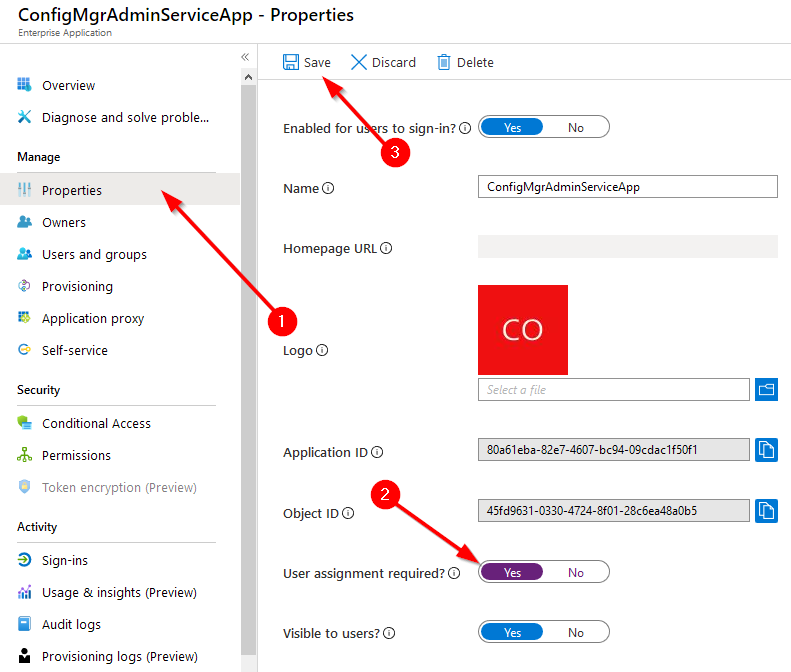
This will force the application to only accept users or groups who are authorized to used the application as defined in the “Users and Groups” tab. Click on the “Users and Groups” tab, click “Add User” and then select the users or groups (Groups require an Azure AD P1 or P2 subscription) you wish to assign to the application.
Now that we’ve assigned permissions to the application, we need to give it permissions to access the CMG application. By default the API permissions given to a new app registration allow the user to sign in and read a user profile. Open the app registration in Azure AD, select “API permissions” and then press “+ Add a permission”
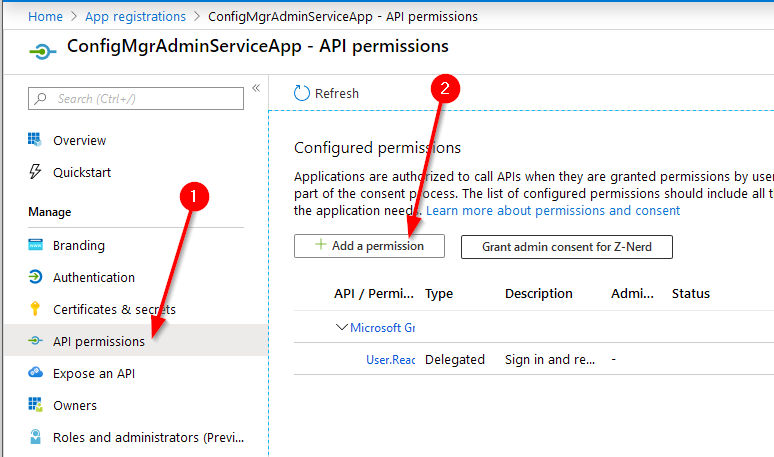
Click on “APIs my organization uses” and search for the name of the CMG app registration which you created when you setup you CMG. Mine is called “CMG-APP”. Select it, check the box for “user_impersonation” and then press “Add permissions”
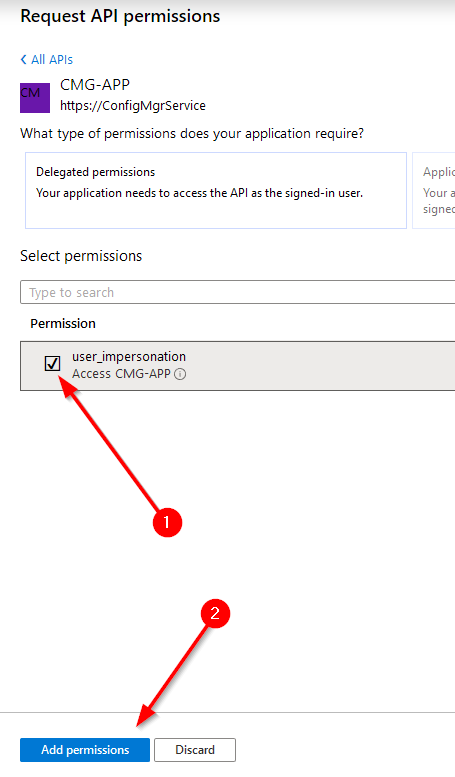
Next, you should grant administrative consent for these permissions on the application. Press the “Grant admin consent for TENANTNAME” button. You’ll be walked through the process of logging in with an administrative account to grant access for your environment.
Next we need to give the app registration a redirection URI. Select the “Authentication” tab, check the box for “https://login.microsoftonline.com/common/oauth2/nativeclient", then click “Save”.
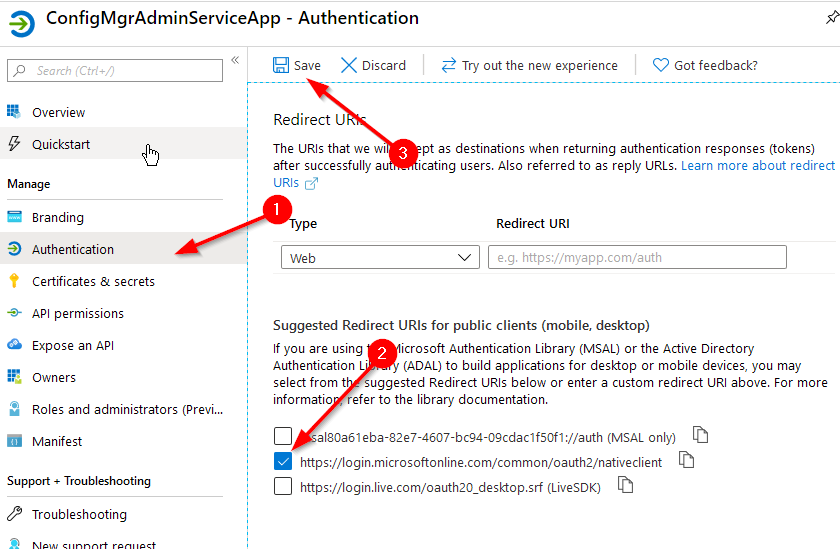
Now you have your app registration completed and secured!
Accessing Data
Now that you have the app registration completed, you can access the AdminService through Cloud Management Gateway. However, the endpoint now only allows access for the users or groups that you have configured. To access the data you just need to submit an authenticated POST request to your CMG endpoint. Instead of re-inventing the wheel here I’m just going to point you at Sandy’s post. Her script is easy to understand and virtually the same thing that I would write.
The Script: https://gist.github.com/sandytsang/d16da8ec0c0c5dad9a27e0933bb534b8#file-adminservice_cmg-ps1
Final Thoughts
This is currently the most “secure” method I know of to lock down access to the AdminService via Cloud Management Gateway. If you know of a better way to secure it please feel free to let me know in the comments below! As always, happy admining!



Share this post
Twitter
Facebook
Reddit
LinkedIn
Email